Cloaking Technology is Bad News
We analyzed a cloaking service today that could potentially enable some disastrous security breaches. The name of the service is "SpoofCard".
The service, available online to anyone, is a spoofing service. It allows anyone with a credit card to sign up and call a number using any phone number you enter (including the phone number of a legitimate business), and a fake voice of your choosing.
Yes, you parsed that "Voice Changer" feature correctly: SpoofCard allows you to disguise your voice while calling on your fake (or spoofed) phone number, and even swap gender.
There are an unlimited number of scenarios I can think of in which this technology would enable a crime to occur, or at least enable the pre-conditions to a crime:
1. Unauthorized voice mail access
2. Business Call Center spoofing
3. Medical Center spoofing
4. Law Enforcement spoofing
5. Bank Call Center spoofing
6. Stalking and abuse
We signed up for SpoofCard and tested several of these scenarios today, using an Authentium corporate mobile BlackBerry connected to the Cingular Network.
The results were unequivocal. The faked phone number went through to my voice mail on the first try (I have since enabled the PIN again - what a pain).
The business spoof was chilling - we used the number of the business and there was no way of telling this was not a legitimate call - and no way of back-channeling the information to find out the caller's identity.
There was no way of knowing that my "bank" was not my actual bank, or my local police station was not my local police station in our testing. The caller ID came up right on-screen, the voice sounded authentic.
Even the female voice disguise (a free option) sounded effective. and at the end of the call, SpoofCard provided an interface to the call history, so I could check out who I'd spammed/scammed: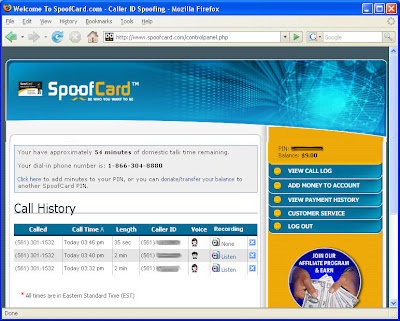
I looked up SpoofCard.com via Whois and of course, like many of the companies in this area, they are using WhoisGuard, and probably a US-based hosting company. No other information was available.
What public good SpoofCard provides, I have no idea. I cannot think of one legitimate reason why this technology should exist.
I also cannot, for the life of me, understand why, during this time of rampant ID fraud and the war on terror, at a time when people are literally dying to protect our assets and way of life, we are not paying closer attention to regulating cloaking technologies that could enable crimes.


2 comments:
"Cloaking" and "spoofing CID" have been going on for a lot longer than most people realize. Anybody with control (authorized or otherwise) of a PBX has been able to do this for ages.
The difference, now, is that the power has been put into the hands of the masses. Unfortunately, the problems that cause this are systemic and not as easy to solve as many people would imagine. The Internet suffers from some similarly "disadvantaged" technology. It will get worse before it gets better because there must be sufficient incentive to change (i.e. new laws + new technology).
I have a very simple suggestion that is worth considering in regard to the VM pin #. What I normally advise people to do is set a VM pin #. You need to do this ANYHOW, because it gives you the option to check your VM from another phone (dial your #, wait for the recording, and hit #pin#).
On many phones you may have your VM # set in more than one place, so you'll need to do it in each location (so that it behaves consistently for you). For example you may have it listed as a contact and it may also be programmed into the "messages" or "voice mail" menu on your phone. The only way to check is to see if the contact for your VM contact has a speed dial set to 1. If it's not set in the contacts, then you'll probably need to change it in a second spot as well.
Make sure that you dial your full 10 digit phone number rather than a shortcut code (like a # or * code) to access your VM . Edit your VM contact(s) to include a pause (or wait) at the end of the 10 digit #, followed by the pin # and pound sign.
Let's assume your MDN is 2105551212 and your VM pin # is 1234:
2105551212P1234#
or
2105551212W1234#
or
2105551212,1234#
or
read your manual :)
There is a different risk resulting from having your pin # stored in the phone. You risk someone getting your VM pin #, but that is easy change. It wouldn't be a bad idea regardless. You might be suprised at some of the information that is retained in your phone without your knowledge. :)
Many handsets allow for password protection. Never forget, if your phone is lost or stolen, immediately call the company to have it suspended because you will liable for any charges if you don't.
It's really very simple, but that's often the case after we look back with regrets.
My girlfriend has a stalker.
He's using this service to really F*ck with her. This needs to be outlawed already. I can see using it for law enforcement but anybody else it's just plain fraud.
I'm thinking of starting a campaign to get this outlawed. Please write your local elected officials.
Post a Comment